Encoding vs. Encryption vs. Tokenization: What Every Engineer Should Know
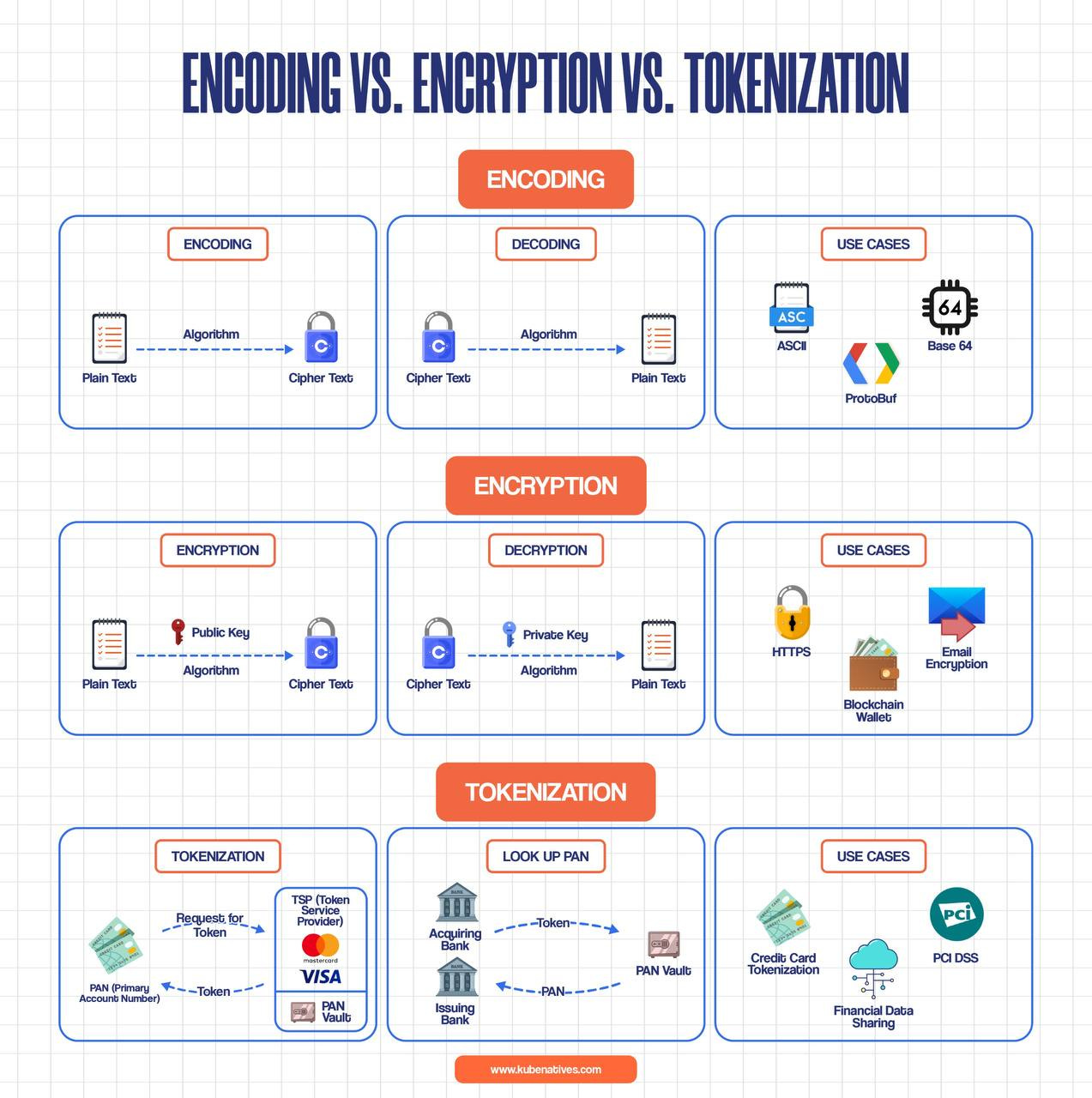
Encoding: Translation, Not Protection
What it is: Converting data from one format to another for compatibility and transmission.
The key insight: Encoding is reversible by design without any keys or secrets. It’s about format, not security.
How it works:
Plain text → Algorithm → Cipher text
Cipher text → Same algorithm → Plain text back
Common examples:
ASCII: Character encoding for text
Base64: Binary-to-text encoding (perfect for embedding images in emails)
ProtoBuf: Efficient binary serialization format
Real-world use case: You’re building an API that needs to transmit binary data over JSON. Base64 encoding lets you embed that binary data as a text string. But remember: anyone can decode it!
⚠️ Critical mistake to avoid: Never use encoding for security. Seeing dXNlcjpwYXNzd29yZA== in your logs? That’s just Base64 for user:password — it takes seconds to decode.
Encryption: Real Security with Keys
What it is: Converting plaintext to ciphertext using cryptographic algorithms and keys to ensure confidentiality.
The key insight: Encryption requires a key to decrypt. Without the right key, the data remains secure (assuming strong algorithms).
How it works:
Plain text + Public key → Algorithm → Cipher text (Encryption)
Cipher text + Private key → Algorithm → Plain text (Decryption)
Common examples:
HTTPS: Securing web traffic
Email encryption: PGP/GPG for confidential communications
Blockchain wallets: Protecting private keys
Database encryption: Protecting data at rest
Real-world use case: Your application stores user passwords. You should encrypt them using a strong algorithm (or better yet, use proper password hashing with bcrypt/Argon2). Even if your database is breached, the encrypted data is useless without the decryption key.
Key types:
Symmetric encryption: Same key for encryption and decryption (AES-256)
Asymmetric encryption: Public key encrypts, private key decrypts (RSA)
Tokenization: Substitution for Sensitive Data
What it is: Replacing sensitive data with non-sensitive surrogate values (tokens) while storing the original data in a secure vault.
The key insight: Tokens have no mathematical relationship to the original data. You can’t reverse-engineer a token to get the original value.
How it works:
Sensitive data (PAN) → Request to Token Service Provider → Receive token
Token stored in your systems
When needed: Send token to vault → Receive original PAN back
Common examples:
Credit card tokenization: PCI DSS compliance for payment processing
PCI DSS: Meeting compliance without storing actual card numbers
Financial data sharing: Sharing transaction data without exposing account numbers
Real-world use case: Your e-commerce platform processes credit cards. Instead of storing 4532-1234-5678-9010, you store token tok_a8f3k2m9x7b1c5d4. Even if hackers breach your database, they can’t use these tokens elsewhere. The actual card numbers live in a PCI-compliant vault.
Why tokenization matters:
Reduces compliance scope (fewer systems handling sensitive data)
Limits blast radius of security breaches
Maintains format (token can match the original data’s format for legacy systems)
Which One Should You Use?
Use Encoding when:
You need data compatibility (binary → text)
You’re transmitting data over protocols that don’t support binary
You’re working with different character sets
NOT for security or protecting sensitive data
Use Encryption when:
You need confidentiality and data protection
You’re storing passwords, secrets, or sensitive information
You’re transmitting data over untrusted networks
Compliance requires data to be encrypted at rest or in transit
Use Tokenization when:
You need to reduce PCI DSS compliance scope
You’re handling credit card or financial data
You want to minimize risk in case of a breach
You need to use sensitive data across multiple systems safely
Real-World Scenario: Building a Payment System
Let’s say you’re building a payment processing system:
Receive payment data → Use HTTPS (encryption in transit)
Store card numbers → Use tokenization (store tokens, not real PANs)
Pass tokens to payment processor → The processor has the vault access
Log transaction IDs → Base64 encode them if needed for transmission (but they’re not sensitive)
This approach means your application never stores actual credit card numbers, dramatically reducing your security and compliance burden.
Common Pitfalls to Avoid
Treating encoding as encryption
// WRONG - This is NOT secure!
const password = btoa(”myPassword123”); // Just Base64 encoding
Use proper encryption
// RIGHT - Actual encryption with a key
const encrypted = CryptoJS.AES.encrypt(password, secretKey);
Encrypting when tokenization is better
If you encrypt credit cards, you still have sensitive data in your system
If you tokenize, you delegate that responsibility to a specialized vault
Rolling your own crypto
Always use established libraries and algorithms
Don’t invent your own encoding/encryption schemes
Deep Dive Resources
Want to learn more? Check out:
NIST guidelines on encryption standards
PCI DSS tokenization requirements
OWASP guidance on secure data storage
Your cloud provider’s key management services (AWS KMS, Azure Key Vault, GCP KMS)
P.S. - Next week: Zero Trust Architecture in Kubernetes. Don’t miss it!