Init Containers: The Setup Crew of Kubernetes
A DevOps Engineer's Guide to Bulletproof Pod Initialization
What You'll Learn Today
Master the init container pattern, understand when and how to use them, and discover real-world scenarios where they save the day. This builds on last week's pause container deep dive.
The Problem: Startup Dependencies
You've been there: your application container starts, but it fails because the database isn't ready, configuration files don't exist, or required services aren't available. Traditional solutions involve complex retry logic, health checks, and brittle startup scripts.
Init containers solve this elegantly by handling all setup tasks before your main application even starts.
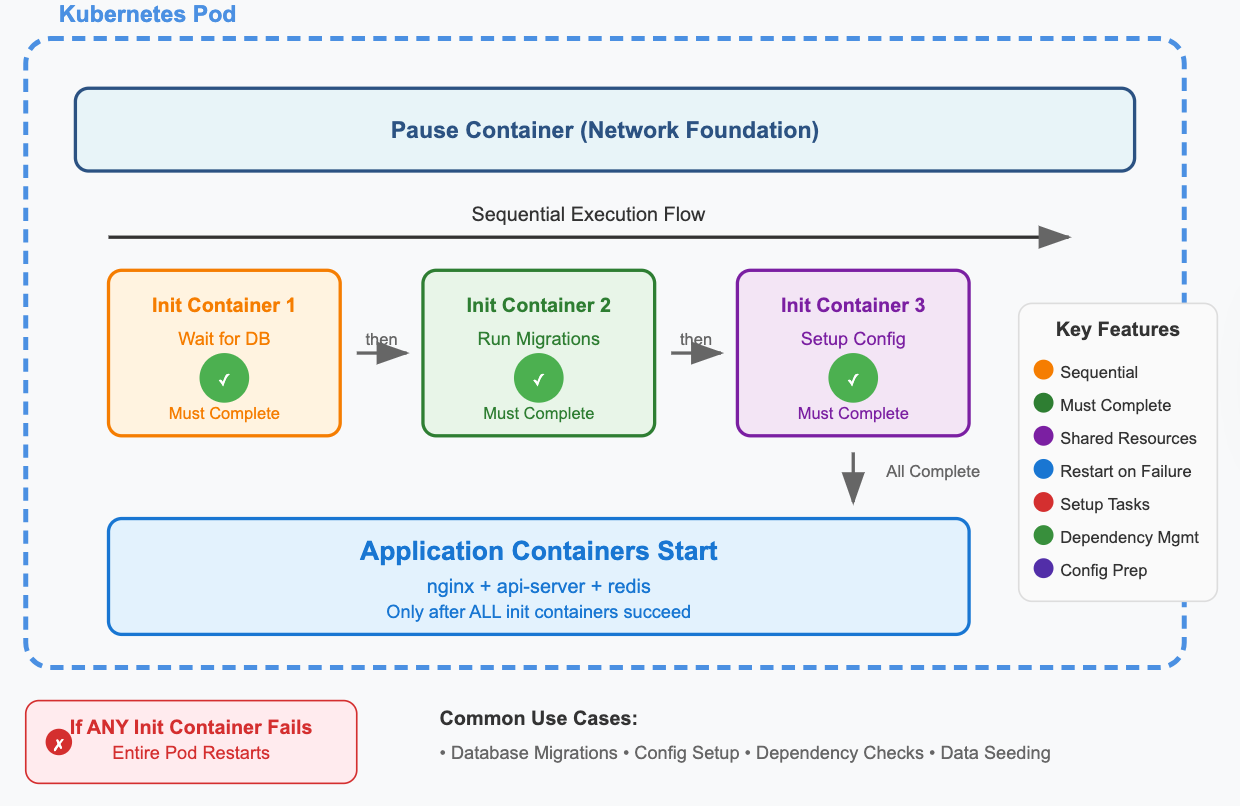
What Are Init Containers?
Init containers are specialized containers that run and complete before your main application containers start. They're like the "setup crew" that prepares everything your application needs to run successfully.
Key Characteristics:
Run to completion: Must finish successfully before app containers start
Sequential execution: Multiple init containers run one after another
Shared resources: Access the same volumes and network as app containers
Failure handling: If any init container fails, the entire pod restarts
How Init Containers Work
The Execution Flow:
Pod Creation: Kubernetes creates the pod and pause container
Init Container Execution: Each init container runs sequentially
Completion Check: Each init container must exit with status 0
App Container Start: Only after all init containers succeed
Failure Handling: Any init container failure restarts the entire pod
Visual Timeline:
Pause Container → Init Container 1 → Init Container 2 → App Containers
↓ ↓ ↓ ↓
(Always runs) (Database setup) (Config prep) (Main app)
Real-World Use Cases
1. Database Migration and Setup
# Wait for database and run migrations
initContainers:
- name: db-migration
image: migrate/migrate
command: ['migrate', '-path', '/migrations', '-database', 'postgres://...', 'up']
2. Configuration Generation
# Generate config files from templates
initContainers:
- name: config-generator
image: my-config-tool
command: ['sh', '-c', 'envsubst < /template/config.tmpl > /shared/config.yaml']
3. Service Dependency Checks
# Wait for external services
initContainers:
- name: wait-for-redis
image: busybox
command: ['sh', '-c', 'until nc -z redis 6379; do sleep 1; done']
4. Data Seeding
# Download and prepare data
initContainers:
- name: data-downloader
image: alpine/curl
command: ['sh', '-c', 'curl -o /data/dataset.json https://api.example.com/data']
Init Container Patterns
Pattern 1: The Waiter
Purpose: Wait for dependencies to be ready Common Use: Database, cache, external APIs
initContainers:
- name: wait-for-db
image: postgres:13
command: ['sh', '-c', 'until pg_isready -h $DB_HOST -p $DB_PORT; do sleep 1; done']
env:
- name: DB_HOST
value: "postgres-service"
- name: DB_PORT
value: "5432"
Pattern 2: The Preparer
Purpose: Set up files, configurations, or data Common Use: Config generation, data downloads
initContainers:
- name: config-preparer
image: busybox
command: ['sh', '-c', 'cp /config-template/* /shared-config/ && chmod 600 /shared-config/*']
volumeMounts:
- name: config-volume
mountPath: /shared-config
Pattern 3: The Validator
Purpose: Check prerequisites and validate environment Common Use: License validation, environment checks
initContainers:
- name: env-validator
image: my-validator
command: ['validate-env']
env:
- name: LICENSE_KEY
valueFrom:
secretKeyRef:
name: app-license
key: license
Pattern 4: The Migrator
Purpose: Run database migrations or data transformations Common Use: Schema updates, data migrations
initContainers:
- name: db-migrator
image: flyway/flyway
command: ['flyway', 'migrate']
env:
- name: FLYWAY_URL
value: "jdbc:postgresql://db:5432/myapp"
Best Practices for DevOps Teams
1. Keep Init Containers Lightweight
Use minimal base images (alpine, scratch)
Include only necessary tools
Avoid complex logic; keep it simple
2. Handle Failures Gracefully
Use proper exit codes (0 for success, non-zero for failure)
Implement timeouts to prevent hanging
Log meaningful error messages
3. Resource Management
Set resource requests and limits
Consider init container resource usage in capacity planning
Use appropriate restart policies
4. Security Considerations
Apply least privilege principles
Use read-only root filesystems where possible
Scan init container images for vulnerabilities
Common Pitfalls and Solutions
Pitfall 1: Init Containers Running Forever
Problem: Init container doesn't exit, blocking pod startup Solution: Implement proper exit conditions and timeouts
initContainers:
- name: wait-for-service
image: busybox
command: ['sh', '-c', 'timeout 300 sh -c "until nc -z service 80; do sleep 1; done"']
Pitfall 2: Resource Hogging
Problem: Init containers consuming excessive resources Solution: Set appropriate resource limits
initContainers:
- name: data-processor
image: my-processor
resources:
requests:
memory: "64Mi"
cpu: "250m"
limits:
memory: "128Mi"
cpu: "500m"
Pitfall 3: Ignoring Init Container Logs
Problem: Debugging pod startup issues without checking init container logs Solution: Always check init container logs first
# Check init container logs
kubectl logs <pod-name> -c <init-container-name>
# Check all init containers
kubectl logs <pod-name> --all-containers=true
Advanced Patterns
Multi-Stage Init Containers
initContainers:
- name: stage1-download
image: alpine/curl
command: ['curl', '-o', '/shared/data.tar.gz', 'https://example.com/data.tar.gz']
- name: stage2-extract
image: alpine
command: ['tar', '-xzf', '/shared/data.tar.gz', '-C', '/shared/']
- name: stage3-validate
image: my-validator
command: ['validate', '/shared/data/']
Init Container with Sidecar Pattern
initContainers:
- name: config-generator
image: my-config-tool
# Generate config for both main app and sidecar
containers:
- name: main-app
image: my-app
- name: log-shipper
image: fluent-bit
# Uses config generated by init container
Monitoring and Observability
Key Metrics to Track:
Init container execution time
Init container failure rates
Resource usage during initialization
Pod startup time (including init containers)
Monitoring Commands:
# Check init container status
kubectl get pods -o wide
# Describe pod to see init container details
kubectl describe pod <pod-name>
# Monitor init container resource usage
kubectl top pods --containers
# Check init container events
kubectl get events --field-selector involvedObject.name=<pod-name>
Init Containers vs Alternatives
Init Containers vs Job/CronJob:
Init Containers: Part of pod lifecycle, run before app containers
Jobs: Independent workloads, run separately from applications
Init Containers vs Liveness/Readiness Probes:
Init Containers: Pre-startup preparation
Probes: Runtime health checking
Init Containers vs Application-Level Retry:
Init Containers: External dependency resolution
App Retry: Internal application resilience
Real-World Example: Complete Pod Definition
apiVersion: v1
kind: Pod
metadata:
name: web-app-with-init
spec:
initContainers:
- name: wait-for-db
image: postgres:13-alpine
command: ['sh', '-c', 'until pg_isready -h postgres -p 5432; do sleep 1; done']
- name: run-migrations
image: migrate/migrate
command: ['migrate', '-path', '/migrations', '-database', 'postgres://user:pass@postgres:5432/db?sslmode=disable', 'up']
volumeMounts:
- name: migrations
mountPath: /migrations
- name: setup-config
image: busybox
command: ['sh', '-c', 'cp /config-template/app.conf /shared-config/ && chmod 644 /shared-config/app.conf']
volumeMounts:
- name: config-template
mountPath: /config-template
- name: shared-config
mountPath: /shared-config
containers:
- name: web-app
image: my-web-app:latest
volumeMounts:
- name: shared-config
mountPath: /etc/app-config
ports:
- containerPort: 8080
volumes:
- name: migrations
configMap:
name: db-migrations
- name: config-template
configMap:
name: app-config-template
- name: shared-config
emptyDir: {}
Troubleshooting Guide
Init Container Stuck in Pending:
Check node resources
Verify image pull secrets
Check volume mounts
Init Container Failing:
Check logs:
kubectl logs <pod> -c <init-container>Verify environment variables
Check network connectivity
Validate file permissions
Pod Restart Loop:
Check all init container exit codes
Verify resource limits
Check for deadlocks in init logic
Action Items for This Week
Audit existing deployments: Identify pods that could benefit from init containers
Implement monitoring: Add init container metrics to your observability stack
Create templates: Build reusable init container patterns for common use cases
Update documentation: Document init container patterns for your team
Key Takeaways
Init containers handle setup tasks before your main application starts
They run sequentially and must complete successfully
Perfect for dependency checks, migrations, and configuration setup
Proper resource management and error handling are crucial
They're a key part of building resilient, predictable deployments
Next Week Preview
Next week, we'll explore Sidecar Containers – the companions that run alongside your main application containers. We'll see how they work with both pause and init containers to create powerful, modular architectures.
Questions about init containers or specific implementation challenges? Reply to this newsletter or reach out on LinkedIn or X
Happy initializing!