Understanding DNS: The Internet's Navigation System
Mastering DNS: Your Guide to the Internet's Hidden Navigation Network
In the vast ocean of the internet, where billions of devices connect and communicate daily, a critical system works silently behind the scenes, enabling us to navigate easily. This system is the Domain Name System (DNS), often called the "phonebook of the internet."
While most users simply type a website name into their browser and expect instant results, those of us in DevOps, Site Reliability Engineering (SRE), and software development know that a complex infrastructure makes this seemingly simple action possible.
As technical professionals responsible for building, maintaining, and optimizing digital infrastructure, understanding DNS is not just beneficial—it's essential. DNS issues can cause widespread outages, security vulnerabilities, and performance bottlenecks.
A thorough understanding of DNS can help you design more resilient systems, troubleshoot complex networking problems, and implement modern architectural patterns effectively.
By the end of this newsletter, you'll have a comprehensive understanding of DNS that will enhance your ability to design, implement, and troubleshoot complex systems. Let's begin our journey through one of the internet's most fundamental technologies.
DNS Fundamentals: The Backbone of Internet Navigation
What is DNS and Why it Exists ?
The Domain Name System (DNS) is a hierarchical, distributed database that serves as the foundation for name resolution on the Internet. At its core, DNS exists to solve a fundamental usability problem: while computers communicate using numerical IP addresses (such as 192.168.1.1 or 2001:0db8:85a3:0000:0000:8a2e:0370:7334), humans find it much easier to remember names (like google.com or github.com).
Before DNS, the mapping between hostnames and IP addresses was maintained in a single hosts file (hosts.txt) that was centrally managed and distributed to all connected computers. As the Internet grew from dozens to thousands and eventually millions of hosts, this approach became completely unsustainable. DNS was developed to replace this system with a distributed, hierarchical approach that could scale with the explosive growth of the Internet.
For DevOps engineers and SREs, DNS represents more than just a convenience—it's a critical infrastructure component that enables service discovery, load balancing, failover mechanisms, and many other essential patterns in modern distributed systems. Understanding DNS is crucial for designing resilient, scalable architectures and troubleshooting complex networking issues.
Core Components of the DNS System
The DNS system consists of several key components that work together to provide name resolution services:
DNS Namespace: The hierarchical structure of domain names, organized as an inverted tree with the root at the top. Each node in the tree represents a domain, and each domain can contain subdomains.
DNS Zones: Administrative boundaries within the DNS namespace. A zone is a portion of the DNS namespace that is managed by a specific organization or administrator.
DNS Servers: The servers that store DNS records and respond to queries. There are several types:
Root servers: Manage the root zone and direct queries to the appropriate TLD servers
TLD (Top-Level Domain) servers: Manage domains under specific TLDs like .com, .org, or .net
Authoritative servers: Provide definitive answers for specific domains
Recursive resolvers: Process queries on behalf of clients and interact with the DNS hierarchy
DNS Records: The actual data stored in DNS, including mappings between domain names and IP addresses, mail server information, and other domain-related data.
DNS Clients (Resolvers): Software on end-user devices that initiates DNS queries. This includes the resolver libraries in operating systems and applications.
DNS Protocol: The communication protocol used between DNS clients and servers, typically running over UDP port 53 for standard queries and TCP port 53 for larger responses or zone transfers.
DNS Hierarchy and Architecture
The DNS namespace is organized as a hierarchical, inverted tree structure, with the root (represented as a dot ".") at the top. Below the root are the Top-Level Domains (TLDs), which include:
Generic TLDs (gTLDs): Such as .com, .org, .net, and newer additions like .app, .dev, and .cloud
Country Code TLDs (ccTLDs): Two-letter codes representing countries, like .us (United States), .uk (United Kingdom), or .jp (Japan)
Special-Purpose TLDs: Such as .arpa for infrastructure purposes
Below the TLDs are second-level domains (like google in google.com), which organizations or individuals register. These domain owners can then create subdomains (like mail in mail.google.com) to organize their services.
This hierarchical structure enables the delegation of authority, allowing different organizations to manage their portions of the namespace independently. For example, the Internet Corporation for Assigned Names and Numbers (ICANN) oversees the root zone, while registry operators manage TLDs, and domain owners manage their specific domains.
The distributed nature of DNS is one of its greatest strengths. No single server needs to store the entire database, and the system can continue functioning even if some servers are unavailable. This architecture has proven remarkably scalable, growing from handling a few thousand domains in the 1980s to hundreds of millions today.
For DevOps and SRE professionals, understanding this hierarchy is essential for designing robust DNS configurations, troubleshooting resolution issues, and implementing advanced patterns like split-horizon DNS or multi-region deployments.
The hierarchical, distributed nature of DNS mirrors many modern architectural approaches, making it a familiar model for those working with distributed systems.
The DNS Resolution Process: Behind the Scenes of a Domain Name Lookup
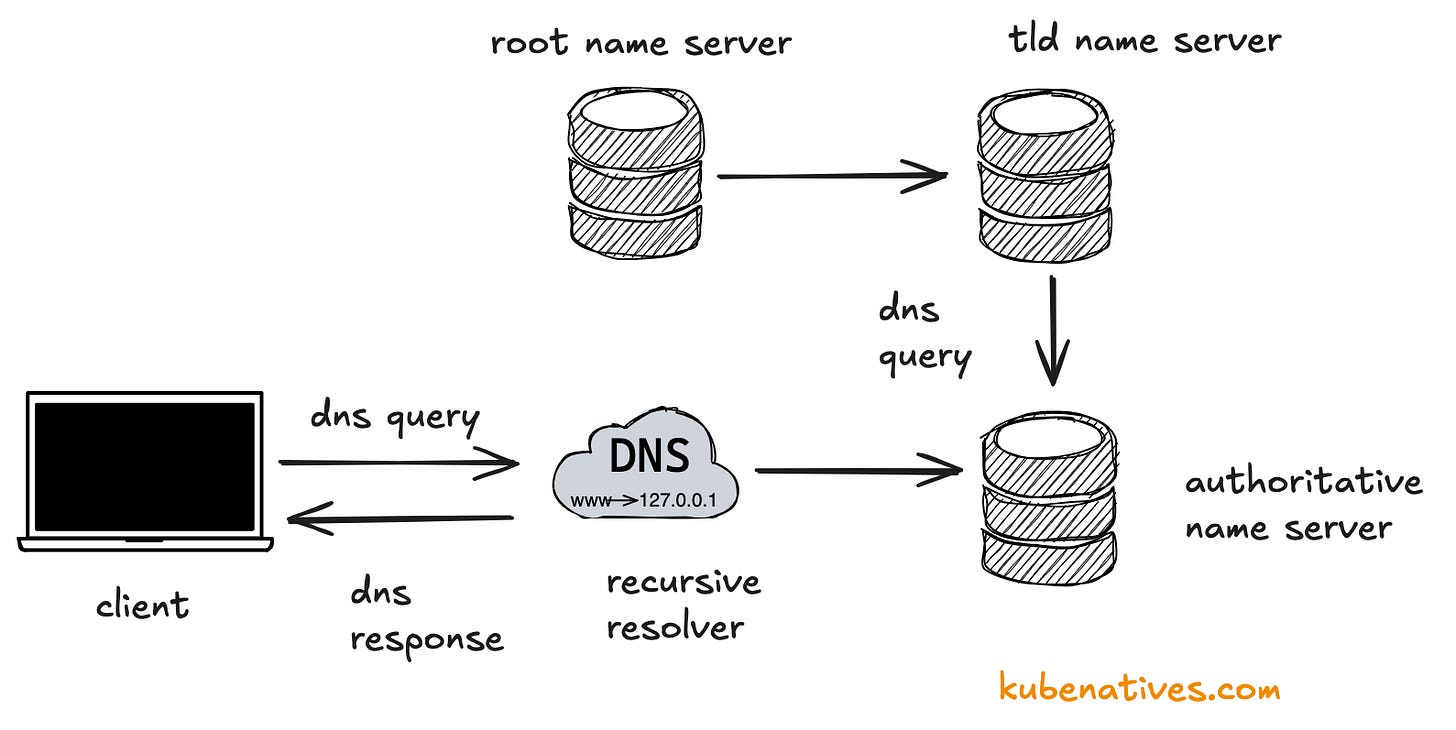
When you type a URL like "www.example.com" into your browser, a complex series of operations begins behind the scenes to translate that human-readable domain name into the IP address needed to establish a connection. This process, known as DNS resolution, typically happens in milliseconds but involves multiple servers and several steps. Let's walk through this process in detail, as understanding it is crucial for diagnosing network issues and optimizing application performance.
The standard DNS resolution process involves the following steps when no information is cached:
1. User Input: A user enters a domain name (like www.example.com) into their web browser.
2. Resolver Query: The browser first checks its own cache for the DNS record. If not found, it sends a request to the operating system's DNS resolver (sometimes called the "stub resolver").
3. OS-Level Resolution: The operating system checks its local DNS cache. If the record isn't found, it forwards the request to the configured DNS resolver, typically provided by your Internet Service Provider (ISP) or a third-party DNS service like Cloudflare's 1.1.1.1 or Google's 8.8.8.8.
4. Recursive Resolver: This DNS server, operated by your ISP or DNS provider, is responsible for finding the answer to your query. If it doesn't have the information cached, it begins a series of queries to other DNS servers.
5. Root Server Query: The recursive resolver first contacts one of the 13 logical root DNS server clusters. These servers don't know the specific IP address you're looking for, but they know where to find the Top-Level Domain (TLD) servers for domains like .com, .org, etc.
6. TLD Server Query: The root server responds with the address of the appropriate TLD server. The recursive resolver then queries this TLD server (e.g., the .com TLD server for example.com).
7. Authoritative Server Query: The TLD server responds with the address of the authoritative nameserver for the specific domain. The recursive resolver then queries this authoritative server.
8. Final Resolution: The authoritative nameserver returns the IP address for the requested domain to the recursive resolver.
9. Response to Client: The recursive resolver returns this information to the operating system, which passes it to the browser.
10. Connection Establishment: With the IP address now available, the browser can establish a connection to the web server and request the webpage.
For DevOps and SRE professionals, understanding this process is invaluable when troubleshooting connectivity issues, as problems can occur at any step. For example, if your authoritative nameservers are misconfigured or unreachable, users won't be able to resolve your domain names, resulting in service unavailability even if your application servers are functioning perfectly.
Types of DNS Queries
DNS resolution involves different types of queries, each serving a specific purpose in the resolution process:
Recursive Queries: In a recursive query, the client (usually an end-user's device) asks a DNS server (the recursive resolver) to either provide the complete answer or indicate that the record doesn't exist. The recursive resolver takes full responsibility for finding the answer, making additional queries as needed. This is the most common type of query from client devices to their configured DNS servers.
Iterative Queries: In an iterative query, the DNS server provides the best answer it currently has, even if it's not the final answer. If the server doesn't know the answer, it returns a referral to another DNS server that might have more information. The client (or recursive resolver) then needs to query that server. This is typically how recursive resolvers interact with the DNS hierarchy (root servers, TLD servers, and authoritative servers).
Non-Recursive Queries: These occur when a DNS server already has the answer, either because it's authoritative for the domain or because the answer is in its cache. The server can respond immediately without making additional queries.
DNS Caching and Its Importance for Performance
DNS caching is a critical optimization that dramatically improves the performance and efficiency of the DNS system. Without caching, every DNS lookup would require the full resolution process described above, resulting in significant latency for users and enormous load on DNS infrastructure.
Caching occurs at multiple levels:
Browser Cache: Modern web browsers maintain their own DNS cache, storing recently resolved domain names to avoid repeated lookups during a browsing session.
Operating System Cache: The operating system maintains a DNS cache that's shared across all applications, reducing the need for external queries.
Recursive Resolver Cache: ISP and third-party DNS resolvers cache responses, allowing them to answer queries for popular domains instantly without consulting other servers.
Time-To-Live (TTL): Each DNS record includes a TTL value that specifies how long it can be cached. TTLs are set by the domain administrator and can range from seconds to days, depending on how frequently the record might change.
For DevOps and SRE professionals, understanding and optimizing DNS caching is essential for performance tuning. Some key considerations include:
TTL Optimization: Setting appropriate TTL values based on your deployment patterns. Lower TTLs allow faster propagation of changes but increase DNS query load; higher TTLs improve performance but slow down updates.
Cache Warming: For critical services, you might implement DNS cache warming strategies to ensure resolvers have your records cached before users need them.
Cache Poisoning Protection: Implementing security measures like DNSSEC to prevent cache poisoning attacks, where attackers inject fraudulent records into DNS caches.
Monitoring Cache Hit Rates: Tracking DNS cache performance metrics to identify opportunities for optimization.
Effective DNS caching strategies can significantly reduce latency for your users and decrease the load on your authoritative nameservers, contributing to a better overall user experience.
Common DNS Resolution Issues and Troubleshooting
Despite its robust design, DNS resolution can encounter various issues that impact service availability and performance. Here are some common problems and troubleshooting approaches:
DNS Propagation Delays: When you update DNS records, changes don't take effect immediately everywhere due to caching.
Troubleshooting tip: Check the TTL values on your records before making changes, and plan accordingly for propagation time.Nameserver Failures: If your authoritative nameservers are unreachable, DNS resolution fails.
Troubleshooting tip: Implement redundant nameservers across different network providers and geographic regions.Misconfigurations: Incorrect DNS records can cause resolution failures or direct traffic to the wrong destinations.
Troubleshooting tip: Use DNS validation tools to verify your zone configurations before deployment.DNS Hijacking: Malicious actors may attempt to redirect DNS queries to fraudulent servers.
Troubleshooting tip: Implement DNSSEC and monitor for unexpected DNS changes.Resolver Performance Issues: Slow or overloaded DNS resolvers can degrade user experience.
Troubleshooting tip: Consider using high-performance public DNS services or implementing your own resolver infrastructure for critical applications.NXDOMAIN Responses: These indicate that the domain doesn't exist according to authoritative servers.
Troubleshooting tip: Verify domain registration and nameserver delegation.SERVFAIL Responses: These indicate a server failure during resolution.
Troubleshooting tip: Check for DNSSEC validation failures, nameserver connectivity issues, or zone configuration problems.For effective DNS troubleshooting, several tools are invaluable:
dig/nslookup/host: Command-line utilities for querying DNS servers directly
DNSViz: Visualizes the DNSSEC authentication chain
DNS Benchmark tools: Measure resolver performance
Packet analyzers: Like Wireshark for examining DNS traffic at the protocol level
Online DNS checkers: Verify your DNS configuration from multiple global locations
DNS Record Types: The Building Blocks of Domain Configuration
Overview of Common DNS Record Types
A Records (Address Records): The most basic and common DNS record type, A records map a domain name to an IPv4 address.
For example, an A record might map example.com to 93.184.216.34. These records are essential for basic web hosting and most internet services.
AAAA Records (IPv6 Address Records): Similar to A records but for IPv6 addresses. As IPv6 adoption continues to grow, AAAA records are becoming increasingly important.
They map domain names to IPv6 addresses like 2606:2800:220:1:248:1893:25c8:1946.
CNAME Records (Canonical Name Records): These records create an alias from one domain name to another. For example, a CNAME record might point www.example.com to example.com, allowing both to resolve to the same destination.
CNAMEs are particularly useful for services like CDNs or when you need multiple subdomains to point to the same destination.
MX Records (Mail Exchange Records): MX records specify the mail servers responsible for accepting email for a domain. They include a priority value to indicate the order in which mail servers should be tried. For example, an MX record might direct email for example.com to mail.example.com with priority 10.
TXT Records (Text Records): These versatile records store text information associated with a domain. They're commonly used for domain verification (proving ownership to third-party services).
SPF records (defining authorized email senders), and DKIM (email authentication). TXT records have become increasingly important for security and service integration.
NS Records (Name Server Records): NS records specify the authoritative DNS servers for a domain. They're crucial for the DNS delegation process, telling the internet which servers to query for authoritative information about a domain.
SOA Records (Start of Authority Records): Every DNS zone must have exactly one SOA record, which contains administrative information about the zone, including the primary nameserver, the administrator's email address, the serial number (for zone transfers), and various timing parameters.
PTR Records (Pointer Records): Used for reverse DNS lookups, PTR records map an IP address to a domain name—the opposite of what A and AAAA records do. They're commonly used for email validation and logging.
SRV Records (Service Records): These records specify the location of services, including the hostname, port, and priority. They're widely used for VoIP, instant messaging, and other services that need service discovery.
CAA Records (Certification Authority Authorization): CAA records specify which certificate authorities (CAs) are allowed to issue SSL/TLS certificates for a domain, adding an extra layer of security to certificate issuance.
DNSKEY, DS, RRSIG Records: These record types are used for DNSSEC (DNS Security Extensions) to provide authentication and integrity verification for DNS data.
When to Use Specific Record Types
Choosing the right DNS record type for a particular situation is crucial for optimal functionality and performance. Here are some guidelines for when to use specific record types:
Use A and AAAA Records When:
You need to point a domain directly to a specific IP address
You're configuring the "apex" or "naked" domain (e.g., example.com without www)
You need maximum compatibility with all DNS implementations
You want to implement round-robin DNS load balancing by creating multiple A records
Use CNAME Records When:
You want multiple subdomains to point to the same destination
You're using a third-party service that might change its IP addresses (like CDNs or cloud providers)
You need to redirect a subdomain to another domain
Note that CNAME records cannot be used at the apex (root) of a domain according to DNS standards, though some DNS providers offer workarounds like ALIAS or ANAME records.
Use MX Records When:
You're setting up email for your domain
You need to specify backup mail servers with different priorities
You're using a third-party email provider
Use TXT Records When:
You need to verify domain ownership for a service
You're implementing email security standards like SPF, DKIM, or DMARC
You need to store arbitrary text information associated with your domain
Use NS Records When:
You're delegating a subdomain to different nameservers
You're changing your domain's authoritative nameservers
You're setting up a DNS zone
Use SOA Records When:
You're configuring a new DNS zone (though this is typically handled automatically by your DNS provider)
You need to adjust zone transfer parameters or refresh intervals
Use PTR Records When:
You need reverse DNS for your IP addresses (often required for mail servers)
You're managing reverse DNS zones for your IP blocks
Use SRV Records When:
You're deploying services that rely on SRV records for discovery (like Microsoft Active Directory, SIP, XMPP)
You need to specify port numbers and priorities for services
Best Practices for DNS Record Management
Effective DNS record management is crucial for maintaining reliable, secure, and performant services. Here are some best practices that DevOps and SRE professionals should follow:
Documentation and Version Control:
Document all DNS records and their purposes
Store DNS configurations in version control systems
Use infrastructure as code tools to manage DNS records
Implement change management processes for DNS updates
Security Considerations:
Implement DNSSEC to protect against DNS spoofing and cache poisoning
Use CAA records to restrict which certificate authorities can issue certificates for your domains
Implement proper SPF, DKIM, and DMARC records to prevent email spoofing
Limit zone transfer capabilities to only necessary servers
Performance Optimization:
Distribute authoritative nameservers geographically for lower latency
Use anycast addressing for DNS servers to improve resilience and performance
Implement proper caching strategies with appropriate TTL values
Consider using a managed DNS provider with a global anycast network
Redundancy and Reliability:
Use multiple nameservers across different providers and networks
Implement secondary DNS services as a backup
Ensure NS records list at least two nameservers (preferably more)
Test failover scenarios regularly
Monitoring and Maintenance:
Regularly audit DNS records for accuracy and security
Monitor DNS resolution times and success rates
Set up alerts for critical DNS changes or failures
Perform regular health checks on authoritative nameservers
Standardization:
Establish naming conventions for records
Standardize TTL values based on record types and purposes
Create templates for common DNS configurations
Develop clear processes for DNS record lifecycle management
TTL Optimization Strategies
Time-To-Live (TTL) values determine how long DNS records can be cached by resolvers before they need to be queried again. Optimizing TTLs is a balancing act between performance and flexibility:
Strategic TTL Planning:
Use longer TTLs (24+ hours) for stable records that rarely change, like MX records
Use medium TTLs (1-6 hours) for standard A/AAAA records in stable environments
Use shorter TTLs (5-30 minutes) for records that might need to change quickly
Use very short TTLs (30-60 seconds) when preparing for imminent changes or during migrations
TTL Strategies for Different Scenarios:
For Planned Changes:
Lower the TTL well in advance of the planned change (at least 2-3 times the current TTL value)
Wait for the original TTL to expire to ensure all caches have the new, shorter TTL
Make your DNS change
After confirming everything works, gradually increase the TTL back to normal values
For Disaster Recovery:
Maintain relatively short TTLs for critical services to enable faster failover
Consider automated TTL management as part of your DR procedures
Test the actual time it takes for TTL changes to propagate in your environment
For Load Balancing:
When using DNS-based load balancing, shorter TTLs provide more responsive load distribution
Balance TTL length against the increased query load on your nameservers
For CDN and Edge Deployments:
Coordinate TTL strategies with your CDN provider
Consider longer TTLs for static content and shorter TTLs for dynamic services
Monitoring TTL Effectiveness:
Track the actual cache behavior across different resolvers
Monitor the query load on your authoritative nameservers
Analyze the relationship between TTL values and DNS query patterns
Adjust TTL strategies based on observed behavior and performance metrics
DNS for DevOps and SRE: Building Reliable, Secure, and Scalable Infrastructure
DNS Monitoring and Observability
Effective monitoring of DNS infrastructure is critical for maintaining service reliability. DNS failures can have widespread impacts, often affecting multiple services simultaneously, yet they can be challenging to diagnose without proper observability. A comprehensive DNS monitoring strategy should include:
Performance Monitoring: Track key metrics like query response times, query volumes, and success rates. These metrics can help identify performance degradation before it becomes user-impacting.
Availability Monitoring: Regularly check that your authoritative nameservers are reachable and responding correctly to queries. External monitoring from multiple geographic locations is particularly valuable.
Record Validation: Periodically verify that your DNS records are configured correctly and returning the expected values. This can catch unauthorized or incorrect changes.
Propagation Monitoring: During planned DNS changes, monitor the propagation of updates across the internet to ensure changes are taking effect as expected.
Security Monitoring: Watch for unusual query patterns that might indicate DNS-based attacks like DNS amplification or cache poisoning attempts.
Several tools and approaches can help implement effective DNS monitoring:
Specialized DNS Monitoring Services: Services like DNSPerf, Catchpoint, and Constellix offer dedicated DNS monitoring capabilities, including global testing networks.
General-Purpose Monitoring Tools: Platforms like Prometheus, Grafana, Datadog, and New Relic can be configured to monitor DNS metrics and generate alerts.
DNS-Specific Tools: Utilities like DNSViz, Zonemaster, and DNSCheck provide specialized DNS validation and troubleshooting capabilities.
Custom Probes: Many organizations implement custom monitoring scripts that perform regular DNS lookups and validate responses against expected values.
Key metrics to monitor include:
Query response times (both average and percentiles)
Query success rates and error types
Query volumes by record type and domain
Cache hit rates for recursive resolvers
DNSSEC validation success rates
Zone transfer completion and timing
TTL compliance across resolvers
High Availability DNS Configurations
DNS is often the first point of failure in a service chain, making high availability DNS configurations essential for reliable operations. A robust, highly available DNS architecture typically incorporates several key elements:
Multiple Authoritative Nameservers: DNS standards recommend at least two nameservers for each domain, but for critical services, four or more distributed servers provide better resilience. These should be:
Geographically distributed across different regions
Hosted on different network providers
Running different DNS server implementations when possible (to avoid common vulnerabilities)
Anycast DNS: Anycast addressing allows multiple servers to share the same IP address, with network routing directing queries to the topologically closest server. This provides:
Lower latency for users worldwide
Built-in load balancing
Improved DDoS resistance through distributed capacity
Seamless failover if individual nodes become unavailable
Secondary DNS Services: Implementing a secondary DNS provider that receives zone transfers from your primary provider adds an additional layer of redundancy. If your primary DNS provider experiences an outage, the secondary provider can continue serving your DNS records.
DNS Performance Optimization Techniques
Optimizing DNS performance can significantly improve overall application responsiveness, as DNS lookups often occur before any other application communication. Several techniques can help maximize DNS performance:
Strategic TTL Management: Carefully tune Time-To-Live values based on the stability and criticality of records:
Use longer TTLs for stable records to maximize caching
Use shorter TTLs for records that might need to change quickly
Consider different TTL strategies for different record types
DNS Prefetching: Implement DNS prefetching hints in web applications to resolve domains before they're actually needed.
Response Rate Limiting: Implement response rate limiting on authoritative nameservers to prevent abuse while ensuring legitimate queries are processed efficiently.
Query Minimization: Configure recursive resolvers to use query minimization (RFC 7816) to improve privacy and potentially reduce query loads.
Nameserver Infrastructure Scaling: Ensure your authoritative nameservers have sufficient capacity:
Scale horizontally by adding more nameserver instances
Use high-performance DNS server software
Optimize server configurations for your specific query patterns
Consider specialized DNS appliances for high-volume needs
Caching Optimization:
Implement layered caching architectures
Use stale cache handling (serve stale records during outages)
Consider negative caching tuning for non-existent domains
Protocol Optimizations:
Implement DNS over TLS (DoT) or DNS over HTTPS (DoH) with proper connection reuse
Enable TCP Fast Open for DNS transport when supported
Consider implementing DNS cookies (RFC 7873) to reduce the impact of spoofed queries
When optimizing DNS performance, measure the impact of changes using metrics like:
Query response time (both average and percentiles)
Time to first byte for web applications
DNS resolution success rates
Cache hit ratios
Server resource utilization
DNS Security Best Practices
DNS security is critical for protecting both your infrastructure and your users. Several key technologies and practices can help secure your DNS operations:
DNSSEC (DNS Security Extensions): DNSSEC adds cryptographic signatures to DNS records, allowing resolvers to verify their authenticity and protect against cache poisoning and spoofing attacks.
Implementing DNSSEC involves:
Generating key pairs for your zones
Signing your DNS records
Publishing the appropriate DS records in the parent zone
Regular key rotation and management
DNS over HTTPS (DoH) and DNS over TLS (DoT): These protocols encrypt DNS queries between clients and resolvers, protecting against eavesdropping and manipulation:
DoH encapsulates DNS queries in HTTPS, making them indistinguishable from regular web traffic
DoT uses a dedicated TLS connection for DNS queries
Consider implementing both for maximum client compatibility
Access Controls and Rate Limiting: Protect your DNS infrastructure from abuse:
Implement TSIG (Transaction Signature) for zone transfers
Restrict zone transfers to specific IP addresses
Apply rate limiting to prevent DoS attacks
Use ACLs to restrict recursive query access to legitimate clients
Monitoring and Threat Detection: Implement systems to detect DNS-based attacks:
Monitor for unusual query patterns or volumes
Watch for DNS tunneling attempts
Detect and block DNS amplification attacks
Implement DNSSEC validation monitoring
DNS Configuration Hardening:
Disable recursive resolution on authoritative nameservers
Implement response policy zones (RPZs) to block malicious domains
Minimize information disclosure in responses
Regularly update DNS server software to patch vulnerabilities
Operational Security Practices:
Implement strict access controls for DNS management
Use multi-factor authentication for DNS control panels
Maintain detailed audit logs for DNS changes
Regularly review and validate DNS configurations
Implement change management processes for DNS updates
DNS-Based Security Controls:
Implement SPF, DKIM, and DMARC records to prevent email spoofing
Use CAA records to control certificate issuance
Consider DANE (DNS-Based Authentication of Named Entities) for additional TLS verification
By implementing these DNS security best practices, you can protect your infrastructure from a wide range of threats while ensuring reliable service for legitimate users. Remember that DNS security is not a one-time implementation but an ongoing process requiring regular updates, monitoring, and adaptation to emerging threats.
Thank you for joining us on this deep dive into DNS. I hope this newsletter has provided valuable insights that you can apply in your role. As always, I welcome your feedback and suggestions for future topics.
Until next time, happy engineering!
Sharon Sahadevan